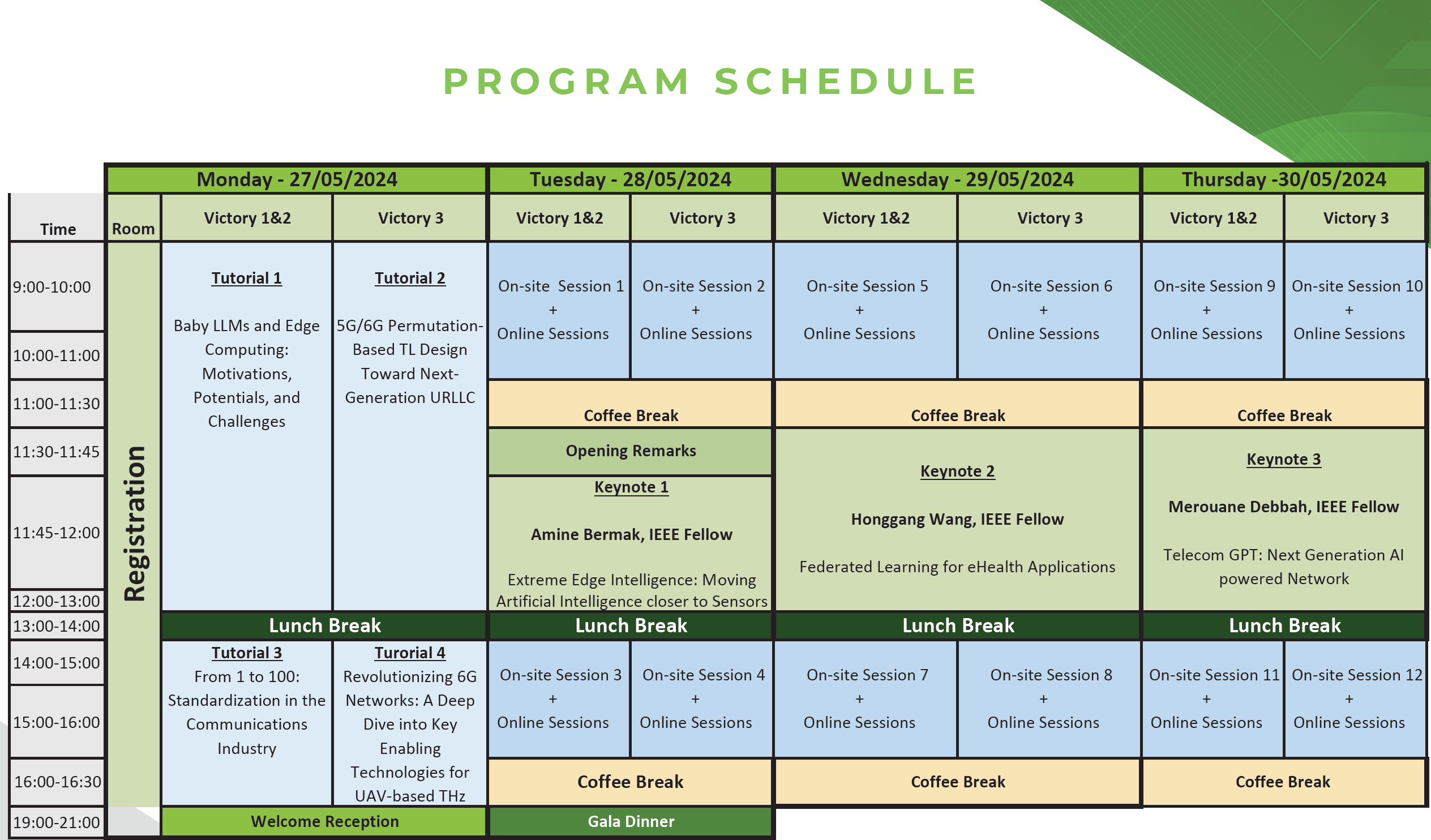
IWCMC 2024 Technical Program
Monday, May 27
Monday, May 27 10:00 - 13:00 (Asia/Nicosia)
Tutorial1: Baby LLMs and Edge Computing: Motivations, Potentials, and Challenges
Ala Al-Fuqaha, Mohamed Abdallah, Mohamed Rahouti, Ruhul Amin, Latif Khan, Shawqi Al-Maliki.
Room: Victory 1&2 | Meeting Link
Chair: Aiman Erbad (Hamad Bin Khalifa University, Qatar) (aerbad@hbku.edu.qa)
Monday, May 27 10:00 - 13:00 (Asia/Nicosia)
Tutorial 2: 5G/6G Permutation-Based TL Design Toward Next-Generation URLLC
Yuli Yang and Mohsen Guizani
Room: Victory 3 | Meeting Link (Passcode: 843342)
Chair: Chrysostomos Chrysostomou (Frederick University, Cyprus) (ch.chrysostomou@frederick.ac.cy)
Monday, May 27 14:00 - 17:00 (Asia/Nicosia)
Tutorial 3: From 1 to 100: Standardization in the Communications Industry
Ruiqi (Richie) Liu and Tianqi Mao
Room: Victory 1&2 | Meeting Link
Chair: Yuli Yang (University of Essex, UK) (yuli.yang@essex.ac.uk)
Monday, May 27 14:00 - 17:00 (Asia/Nicosia)
Tutorial 4: Revolutionizing 6G Networks: A Deep Dive into Key Enabling Technologies for UAV-based THz in High-Performance Fronthaul
Muhammad Shehab, Mazen Hasna, Tamer Khattab, and Nizar Zorba
Room: Victory 3 | Meeting Link
Chair: Tamer Khattab, QU, Qatar (tkhattab@qu.edu.qa)
Tuesday, May 28
Tuesday, May 28 9:00 - 11:00 (Asia/Nicosia)
On-site Session 1
B5G and 6G
Room: Victory 1&2
Chair: Muhammad Absaruddin, ATU Donegal, Ireland, (L00177821@atu.ie)
- 9:00 Communication-efficient Decentralised Federated Learning via Low Huffman-coded Delta Quantization Scheme
- 9:20 Optimizing Shapley Value for Client Valuation in Federated Learning through Enhanced GTG-Shapley
- 9:40 Hyperparameter Impact on Computational Efficiency in Federated Edge Learning
- 10:00 Handling Imbalanced 5G and Beyond Network Tabular Data Using Conditional Generative Models
- 10:20 5G RAN service classification using Long Short Term Memory Neural Network
Tuesday, May 28 9:00 - 11:00 (Asia/Nicosia)
On-site Session 2
Security I
Room: Victory 3
Chair: Ala Gouissem, UDST, Qatar, (ala.gouissem@udst.edu.qa)
- 9:00 Network-based Intrusion Detection Through Image-based CNN and Transfer Learning
- 9:20 Analysis of Physical Layer Security Based on WFRFT with Multiple Eavesdroppers
- 9:40 Node Compromising Detection to Mitigate Poisoning Attacks in IoT Networks
- 10:00 Rule Based Maliciousness Detection in Computer Network using Machine Learning in Fog Node
- 10:20 Detection and positioning of vulnerable road users in vehicular networks
- 10:40 Multi-Domain Scaling Algorithm with Inter-Orchestrator Communication for Beyond 5G/6G Networks
Tuesday, May 28 9:00 - 11:00 (Asia/Nicosia)
Online Session 1
5G, Wireless, Physical
Room: Meeting Link (Passcode: 488190)
Chair: Chrysostomos Chrysostomou, Frederick University, Cyprus, (ch.chrysostomou@frederick.ac.cy)
- 9:00 Non-Line of Sight Detection Based on 5G Signal Strength- and Quality Measurements and its impact on mobile positioning accuracy
- 9:12 Massive MIMO technology a key advancement in shaping communication networks for the 5G/5G+ era
- 9:24 Spectrum Sharing Technologies in the 5G Era Innovative Applications and Challenges in the FDD Band
- 9:36 Research and Application of Multi-Access Collaboration Technology in 6G Networks
- 9:48 Impact Assessment of IAB and Small 5G Stations on Railway Network Communications
- 10:00 Mobility management in 5G and 6G satellite access networks
- 10:12 Interference compatibility study and interference management for 5G and Broadband TDD Private Networks
- 10:24 Network Slicing and its Impact on 5G Data Traffic and Performance
- 10:36 Handover Management in a Sliced 5G Network Using Deep Reinforcement Learning
- 10:48 Deep Reinforcement Learning for Sleep Control in 5G and Beyond Radio Access Networks: An Overview
Tuesday, May 28 9:00 - 11:00 (Asia/Nicosia)
Online Session 2
5G and 6G
Room: Meeting Link
Chair: Antonino Masaracchia, Queen's University Belfast, (antonino.masaracchia@gmail.com)
- 9:00 Research on Key Technologies of 6G Network Architecture
- 9:12 Cross-Domain AI Towards 6G: Requirements, Solution, and Validation
- 9:24 Energy Consumption Evaluation of OMA vs NOMA for Sustainable Scheduling in 6G O-RAN
- 9:36 Orthogonal Chirp Division Multiplexing Waveform Design for 6G mmWave UAV Integrated Sensing and Communication
- 9:48 Design of Base Station Sleeping Scheme in Heterogeneous Cellular Networks Based on User Traffic and SINR
- 10:00 Scaled Conjugate Gradient Algorithm Study for 6G Full Duplex Wireless Communication System
- 10:12 Enhancing Traffic Load Forecasting in 5G Networks: A Statistical and Temporal Feature Engineering Approach
- 10:24 PHD Filter-Based Spatial-Temporal Calibration of 5G Base Stations for Urban Canyon Localization
- 10:36 6G-enabled Situation-Aware ML-assisted UTM (6G-SAMU)
- 10:48 Improving Response Prediction: Transformer Integration and Optimizer Evaluation
Tuesday, May 28 9:00 - 11:00 (Asia/Nicosia)
Online Session 3
- 9:00 Edge-Accelerated UAV Operations: A Case Study of Open Source Solutions
- 9:12 Enhancing Post-Disaster Survivor Detection Using UAV Imagery and Transfer Learning Strategies
- 9:24 Intelligent DWC Reservation and Trip Planning of CAEV and UAV for 6G ITS
- 9:36 UAV Path Planning for Aviation Optimazition Based on Doubly Decoupled Reinforced Network
- 9:48 Secure Status Updates for Internet of Drones: A Deep Q-Learning-Based Antenna Selection Approach
- 10:00 Ultra-Reliable and Low-Latency UAV Communications in High-Mobility Environments
- 10:12 Collaborative Multi-Agent Jamming Deceiving for UAV-assisted Wireless Communications
- 10:24 Communication-Efficient Topology Orchestration for Distributed Learning in UAV Networks
- 10:36 Joint Optimization of User Association, UAV Placement, and Power Allocation in UAV-Satellite-Assisted Cell-Free mMIMO Systems
- 10:48 A Cooperative C-V2X System with UAV-aided Enhanced Connectivity
Tuesday, May 28 9:00 - 11:00 (Asia/Nicosia)
Online Session 4
Vehicular Applications and Edge Computing
Room: Meeting Link (Passcode: 802878)
Chair: Latif Khan, MBZUAI, UAE, (Latif.khan@mbzuai.ac.ae)
- 9:00 End-to-End Spatio-temporal Latency Prediction for Vehicular Applications
- 9:13 Usecase-based generic framework for data fusion and decision making in Autonomous Driving
- 9:26 Evaluation of LSTM GAN for Trajectory Prediction in Connected and Autonomous Vehicles
- 9:39 Actor-Critic Deep RL for Vehicular Edge Computing Optimization
- 9:53 Cost-Efficient Computation Offloading in VEC Using Deep Reinforcement Learning Techniques
- 10:06 Balancing Energy Consumption and Latency in Vehicle Edge Computing for 6G Networks
- 10:19 A Green IoT-Integrated AI-Based EV Scheduling Scheme for Efficient Charging Station Selection
- 10:33 Efficient IoV-Based Geofencing Model for V2X Communication Using Energy Saving Approach
- 10:46 Real-Time Binary Cell Phone Usage Detection and Classification on Vehicular Edge Devices
- 14:59 Decentralized Spectrum Sharing Networks Based on Blockchains
Tuesday, May 28 11:45 - 13:00 (Asia/Nicosia)
Keynote 1: Extreme Edge Intelligence: Moving Artificial Intelligence closer to Sensors
Amine Bermak, IEEE Fellow
Room: Victory 1&2 | Meeting Link (Passcode: 252209)
Chair: Lambros Lambrinos, Cyprus University of Technology, Cyprus, (lambros.lambrinos@cut.ac.cy)
Tuesday, May 28 14:00 - 16:00 (Asia/Nicosia)
On-site Session 3
Security II
Room: Victory 1&2
Chair: Kai Li, University of Cambridge, UK & CISTER, Portugal, (kai@isep.ipp.pt)
- 14:00 Physical Layer Security Meets Privacy Requirements for Downlink NOMA
- 14:20 Exploring LSTM-assisted A2C For Physical Layer Security in Vehicular Cyber-Physical Systems
- 14:40 A Life-long Learning Intrusion Detection System for 6G-Enabled IoV
- 15:00 Optimizing QoS of the LTE network using a machine-learning-based spatio-temporal distribution and Tabu search metaheuristic
- 15:20 A Research Environment for Evaluating File-based Cryptojacking Detection Techniques
- 15:40 CTIoT: A Cyber Threat Intelligence Tool for IoT
Tuesday, May 28 14:00 - 16:00 (Asia/Nicosia)
On-site Session 4
CyberSecurity
Room: Victory 3
Chair: Muhammad Absaruddin, ATU Donegal, Ireland, (L00177821@atu.ie)
- 14:00 An seL4-based Trusted Execution Environment on RISC-V
- 14:20 Lightweight Image Crypto-Compression Using Haar Transform and Selective Encryption for Grayscale IoT Images
- 14:40 Unsupervised Learning Approach for Network Traffic Classification
- 15:00 AI-Driven Fast and Early Detection of IoT Botnet Threats: A Comprehensive Network Traffic Analysis Approach
- 15:20 Thwarting Cybersecurity Attacks with Explainable Concept Drift
- 15:40 Reinforcement Learning-Based Genetic Algorithm for Differentiated Traffic Scheduling in Industrial TSN-5G Networks
Tuesday, May 28 14:00 - 16:00 (Asia/Nicosia)
Online Session 5
Satellite Systems
Room: Meeting Link
Chair: Zain ul Abideen Tariq, HBKU, Qatar, (zata28228@hbku.edu.qa)
- 14:00 Adaptive Grouping Access Based on Rate-Splitting Multiple Access for Multibeam Satellite System
- 14:12 Sub-Block Level Interference Exploitation Precoding in Satellite Communications
- 14:24 6G Satellite Communication: Key Technologies, Challenges and Trends
- 14:36 Advanced Deep Learning Framework for Improved Wildfire Detection and Aerosol Identification Using Active Satellite Imagery
- 14:48 Technical Analysis of Non-terrestrial Networks
- 15:00 Downlink Coverage Probability In Aerial BASE STATION
- 15:12 Performance Study in Heterogeneous Vehicular Networks Using Dual Connectivity and Deep Reinforcement Learning
- 15:24 Leveraging Transfer Learning with Federated Deep Reinforcement Learning for AV Platoon Control
- 15:36 Wireless Sensing for Structural Health Monitoring of Bridges by Unmanned Aerial Vehicle (UAV) via BLE Communication
- 15:48 A 3-D Geometrical-Based Stochastic Model for Satellite-to-Ground MIMO Channels
Tuesday, May 28 14:00 - 16:00 (Asia/Nicosia)
Online Session 6
Resource Management
Room: Meeting Link
Chair: Aamir Latif, Tallinn University of Technology, (aamir.latif@taltech.ee)
- 14:00 Mobility Management Approach for Co-Orbital Regenerated LEO Satellite
- 14:12 Resource Allocation in LEO Satellites assisted Terrestrial Network for Latency-Sensitive Task
- 14:24 Block-Sparse Learning Enabled Approach Towards Efficient Channel Estimation for Underwater Visible Light Communications
- 14:36 Sparsity-Aware Channel Estimation for Underwater Acoustic Wireless Networks: A Generative Adversarial Network Enabled Approach
- 14:48 Data Source Authentication Protocol for Aviation Broadband Communication System
- 15:00 Optimization Approaches for the Optimal Placement of Electrical Charging Stations
- 15:12 Deep Learning-Driven Resource Allocation for MEC-Enabled UAV Collision Avoidance System
- 15:24 Deep Reinforcement Learning Approach for UAV Search Path Planning In Discrete Time and Space
- 15:36 Resource Allocation for Satellite Communication Network of Emergency Communications in Distribution Network
- 15:48 Deep Learning Based Fault Diagnosis Methods for Satellite Power System
Tuesday, May 28 14:00 - 16:00 (Asia/Nicosia)
Online Session 7
Security I
Room: Meeting Link (Passcode: 873765)
Chair: Yagmur Yigit, Edinburgh Napier University, UK, (yagmur.yigit@napier.ac.uk)
- 14:00 Error-correcting Codes in Communication Systems
- 14:12 ECCIA: An Identity Authentication Scheme against IFAs in NDNs
- 14:24 Network Security Situation Assessment Method Based Eigenvector Centrality
- 14:36 ADS-B Replay Attack Detection using Transformers
- 14:48 Stability Analysis of Deep Neural Networks under Adversarial Attacks and Noise Perturbations
- 15:00 An Efficient Approach for Tampering Attack Detection in WSN Using Blockchain
- 15:12 Enhancing IoT Traffic Detection via Attention Mechanisms Derived from Matrix Eigenvalues and Eigenvectors within Transformer Architectures
- 15:24 Opportunistic Routing and Energy Harvesting in Multi-tier Networks against Jamming Attacks
- 15:36 EM-PAD: An Effective Mechanism for Phishing Attack Detection
- 15:48 On Poisoning Attacks and Defenses for LSTM Time Series Prediction Models: Speed Prediction as an Example
Tuesday, May 28 14:00 - 16:00 (Asia/Nicosia)
Online Session 8
- 14:00 Blockchain and DL-based Brain Tumour Prediction Scheme for Telesurgery Systems in Healthcare 4.0
- 14:12 A Blockchain-assisted Group Handover Authentication Protocol for 5G Wireless Networks
- 14:24 Bridging Economic Model and Blockchain: ZKP Empowered Privacy Preserving Payment Channel with Intermediary Pricing
- 14:36 Semantic Knowledge Consensus for Multi-agent Collaboration: A Naming Game Approach
- 14:48 A cross domain authentication scheme based on blockchain
- 15:00 Optimizing Information Propagation for Blockchain-empowered Mobile AIGC: A Graph Attention Network Approach
- 15:12 Grubbs Test Based Algorithms to Improve the Efficiency of Blockchain Oracles
- 15:24 Task Integrity Checker: A Block Chain - Enabled Trust Management System for Fog Nodes
- 15:36 Lightweight WEB3 interface for secure IoMT-Blockchain integration
- 15:48 xG Security: Zero-Trust and Moving Target Defense in Decentralized Learning Environment
Wednesday, May 29
Wednesday, May 29 9:00 - 11:00 (Asia/Nicosia)
On-site Session 5
Edge Computing
Room: Victory 1&2
Chair: Andreas Andreou, University of Nicosia, Cyprus, (andreou.andreas@unic.ac.cy)
- 9:00 Generative Inference of Large Language Models in Edge Computing: An Energy Efficient Approach
- 9:17 Fog computing-empowered smart systems for latency-sensitive control applications
- 9:34 Routing Edge-Cloud Requests via Multi-Objective Reinforcement Learning
- 9:51 AGORA: A Multi-Provider Edge Computing Resource Management and Pricing Framework
- 10:08 Dataset Collection of Multi-Communication Technologies Monitored in Different Mobility Contexts
- 10:25 Refine and Identify: An Accelerated Iterative Algorithm for Securing Federated Learning
- 10:42 Leveraging V2P communications to improve the VRU's safety
Wednesday, May 29 9:00 - 11:00 (Asia/Nicosia)
On-site Session 6
Physical Communications
Room: Victory 3
Chair: Ala Gouissem, UDST, Qatar, (ala.gouissem@udst.edu.qa)
- 9:00 Pre-Chirp-Domain Index Modulation for Affine Frequency Division Multiplexing
- 9:17 Multicarrier Waveform Design for mmWave/THz Integrated Sensing and Communication
- 9:34 Photon-Counting-Based Ultraviolet Communication System with Self Bit Synchronization Module
- 9:51 Simultaneous Transmission and Null Space Tracking using Interference Feedback for Spatial Division Multiple Access
- 10:08 Radio Frequency Fingerprinting via Deep Learning: Challenges and Opportunities
- 10:25 Temperature-based evaluation and optimization of multi-processor mobile computing
- 10:42 Dynamic Switching Access in Massive Machine Type Communication
Wednesday, May 29 9:00 - 11:00 (Asia/Nicosia)
Online Session 9
Security II
Room: Meeting Link (Copy this invitation and open in Tencent Meeting app (V2.13 or later) to join the meeting)
Chair: Yan Wei, Zhejiang University, China, (redwine447@zju.edu.cn)
- 9:00 AKM-FCCI: Secure Authentication and Key Management Mechanism for Fog Computing-Based IoT-Driven Critical Infrastructure
- 9:15 Synergistic Solution: IDS and Scheduler Harmony for Secure 5G Radio Resources
- 9:30 An Enhanced Authentication Protocol for IoT-AmI Environment
- 9:45 Fall Detection Wristband with Optimized Security and Health Monitoring
- 10:00 DoS Attack Detection in VANET using Transfer Learning Approach for BSM Data
- 10:15 MavSec: A safer version of MavLink
- 10:30 Domain adaptive deep semi-supervised transfer learning for anomaly detection in OpenWiFi
- 10:45 A Hybrid Machine Learning Intrusion Detection System for Wireless Sensor Networks
- 11:00 Dynamic Bandwidth Allocation in MIMO 5G Networks
- 11:15 Towards Efficient Urban Network Mobility: A Cloud-Based Ride-Sharing System
Wednesday, May 29 9:00 - 11:00 (Asia/Nicosia)
Online Session 10
Security III
Room: Meeting Link
Chair: Huiyun Xia, Nanjing University of Posts and Telecommunications, (20240028@njupt.edu.cn , summerxiahy@163.com)
- 9:00 Enhancing Security in Multi-Controller SDMN Environments: A Novel 5G Access Authentication Protocol
- 9:12 RFID IoT Architecture for Smart Inventory Management: Security Integration
- 9:24 SERS: Secure & Efficient Random and Symbol Linear Network Coding Schemes
- 9:36 Security for Underground Utility Data Transmission in IoT Sensor Networks
- 9:48 DDoS Attack Prevention in Autonomous Vehicle's OTA Updates: Combining PBFT Consensus and Distributed Firewall in Hyperledger Fabric Blockchain
- 10:00 Deep Learning Dataset Generation for Physical Layer Authentication in Wireless Sensor Networks (WSN)
- 10:12 Towards a Responsive Security Operations Center for UAVs
- 10:24 An Improved Risk Assessment Scheme Balancing Safety and Security
- 10:36 Stealthy Adversarial Attacks on Intrusion Detection Systems: A Functionality-Preserving Approach
Wednesday, May 29 9:00 - 11:00 (Asia/Nicosia)
Online Session 11
- 9:00 DNS flooding attack detection scheme through Machine Learning
- 9:12 Load-Balanced Multipath Routing Through Software-Defined Networking
- 9:24 Deep Reinforcement Learning for IRS-assisted Secure NOMA Transmissions Against Eavesdroppers
- 9:36 Vault-PMS: A Vault-Based Password Management System for Secure Offline Data Storage
- 9:48 Cybersecurity in Smart Renewable Energy Systems
- 10:00 Lightweight CNN-BiLSTM based Intrusion Detection Systems for Resource-Constrained IoT Devices
- 10:12 Defense against Black Hole Attacks in Wireless Sensor Network with Anomaly Report Cycling
- 10:24 An Enhanced Online K-means Algorithm for Flooding Attacks Detection in Vehicular Networks
- 10:36 Securing Next-Generation Networks against Eavesdroppers: FL-Enabled DRL Approach
- 10:48 A Link Adaptive Approach for Federated Learning aided UAV Networks
Wednesday, May 29 9:00 - 11:00 (Asia/Nicosia)
Online Session 12
Traffic Management
Room: Meeting Link (Passcode: 0529)
Chair: Zhiqiang Li, Harbin Institute of Technology, (lizhiqiang0108@foxmail.com)
- 9:00 Advancing IoT Anomalous Traffic Detection through Arithmetic Coding in Transformer-Based Architectures
- 9:12 Collaborative Task Offloading Based on Deep Reinforcement Learning in Heterogeneous Edge Networks
- 9:24 Traffic Counts-based Origin-Destination Matrix Estimation using a Traffic Simulator and Machine Learning
- 9:36 A Comparison of Temporal and Spatio-Temporal Methods for Short-Term Traffic Flow Prediction
- 9:48 A Hidden Parameter study for Traffic-oriented LoRaWAN Deployment
- 10:00 Optimizing Internet Traffic Predictions with a Novel Deep Learning EMD-KNN Framework
- 10:12 Dynamic FlexEthernet Defragmentation Under Time-Varying Traffic in Multi-layer Multi-domain Networks
- 10:24 Temporal Hierarchical Graph Attention Network for Traffic Prediction with Prompt Learning
- 10:36 Dependency-Aware Task Offloading in Cooperative UAV-HAPS-Assisted Vehicular Networks
- 10:48 An Efficient Elastic Scaling, Service Deployment, and Task Allocation Algorithm for Mobile Edge Computing
Wednesday, May 29 11:30 - 13:00 (Asia/Nicosia)
Keynote 2: Federated Learning for eHealth Applications
Honggang Wang, IEEE Fellow
Room: Victory 1&2 | Meeting Link (Passcode: 945237)
Chair: Mohsen Guizani, MBZUAI, UAE, (mguizani@gmail.com)
Wednesday, May 29 14:00 - 16:00 (Asia/Nicosia)
On-site Session 7
Wireless Communications
Room: Victory 1&2
Chair: Muhammad Jamal Shehab, Italy - Politecnico di Torino, Italy, (MuhammadShehab@ieee.org)
- 14:00 Design and Implementation of Recursive Filters using Processing In Memory
- 14:17 Low-Complexity Mean Calculation Schemes Using In Memory Computing
- 14:34 Outage Probability in Network Coding Based Cooperative Wireless Networks over Nakagami-m Fading Channels
- 14:51 Beamwidth Trade-offs Analysis of THz MAC Protocols for Wireless Data Center
- 15:08 Outdoor Environment Reconstruction with Deep Learning on Radio Propagation Paths
- 15:25 Scheduled Trigger Frames: Enabling Worst-case Latency Bounds for Wi-Fi Industrial Use
- 15:42 Proximity Marketing: A Diverse Classification Approach
Wednesday, May 29 14:00 - 16:00 (Asia/Nicosia)
On-site Session 8
Mobility
Room: Victory 3
Chair: Saad EL JAOUHARI, ISEP, France, (saad.el-jaouhari@isep.fr)
- 14:00 Strategic Cooperation in the Metaverse: A Game Theory Analysis with Age of Information
- 14:20 An Air-Sea-Ground Integrated Observation System Based on Ad Hoc Network for the Archipelagic Environment
- 14:40 STEBS: Spatio-Temporal Entropy-Based Scoring Handover Model for LEO Satellite
- 15:20 Experimental Analysis of Chirp Waveforms for Wireless Power Transfer
- 15:40 Effects of Misalignment on Output Voltage Stability in SS Controlled Wireless Power Transfer Systems with Different Control Strategies
Wednesday, May 29 14:00 - 16:00 (Asia/Nicosia)
Online Session 13
Resource Management
Room: Meeting Link (Copy this invitation and open in Tencent Meeting app (V2.13 or later) to join the meeting)
Chair: Yan Wei, Zhejiang University, China, (redwine447@zju.edu.cn)
- 14:00 Resource Management Based on Resource Parameters in Computing Networks
- 14:12 Dynamic Resource Scheduling for Air-Ground Collaborative Communication: A Multi-Agent Method for Metaverse
- 14:24 Conflict Management based on Deep Reinforcement Learning for Edge Computing in Intent-Driven Networks
- 14:36 Online Resource Allocation in Internet of Vehicles Using Topology Attribute-Aware Genetic Algorithm
- 14:48 An Innovative Task Offloading Algorithm Based on Deep Reinforcement Learning in Computation Resource Network
- 15:00 Graph Neural Network Based Resource Allocation for Full-duplex Device-to-Device Communication
- 15:12 Age-Aware Edge Caching and Multicast Scheduling Using Deep Reinforcement Learning
- 15:24 Nash Bargaining Game for Cooperative Resource Allocation in Underwater Acoustic Communication
- 15:36 A Low-Latency Edge-Cloud Serverless Computing Framework with a Multi-Armed Bandit Scheduler
- 15:48 A Comparative Analysis of Data Models for Heterogeneous Sensor Data Management
Wednesday, May 29 14:00 - 16:00 (Asia/Nicosia)
Online Session 14
Federated Learning
Room: Meeting Link (Passcode: 278127)
Chair: Waseem Ullah, MBZUAI, UAE (waseemullah@ieee.org)
- 14:00 Towards the Metaverse: Distributed Radio Map Reconstruction Based on Federated Learning Generative Adversarial Networks
- 14:12 An Efficient and Secure Federated Learning Communication Framework
- 14:24 ERD-FL: Entropy-Driven Robust Defense for Federated Learning
- 14:36 Impact of Neural Network Depth on Split Federated Learning Performance in Low-Resource UAV Networks
- 14:48 Machine-Learning-Based Smart Energy Management Systems: A Review
- 15:00 Federated Active Learning with Transfer Learning: Empowering Edge Intelligence for Enhanced Lung Cancer Diagnosis
- 15:12 A Trust and Data Quality-Based Dynamic Node Selection and Aggregation Optimization in Federated Learning
- 15:24 Energy performance of Internet of Things (IoT) networks for pipeline monitoring
- 15:36 Peer-to-Peer Energy Optimization in V2X Using Reinforcement Learning
- 15:48 RL-Based Incentive Cooperative Data Learning Framework Over Blockchain in Healthcare Applications (RL-ICDL-BC)
Wednesday, May 29 14:00 - 16:00 (Asia/Nicosia)
Online Session 15
Energy Management
Room: Meeting Link
Chair: Hassan Noura, University of Franche-Comté & Institut FEMTO-ST, France, (hassan.noura@univ-fcomte.fr)
- 14:00 Power Allocation and User Pairing Based Beam Reuse in a NOMA System
- 14:12 A Hierarchical PoW-Powered Access Mechanism for Shuffling-Based Moving Target Defense System
- 14:24 Advancing Fairness in Microgrid Energy Transaction: An Alternative Approach
- 14:36 Empowering Energy Consumption Forecasting in Smart Buildings: Towards a Hybrid Loss Function
- 14:48 Power Transmission Assessment for Body Channel Communication
- 15:00 Survey on Demand Response in the Landscape of Adaptive and Intelligent Building Energy Management Systems
- 15:12 Deep Learning Model for Energy Consumption Prediction and Carbon Emission Estimation
- 15:24 Predicting Power Consumption Using Machine Learning Techniques
- 15:36 Fault Classification on Power Transmission Lines Using DC Component Extraction
- 15:48 Dynamic Clustering-based Task Orchestrator in Mobile Edge Computing
Wednesday, May 29 14:00 - 16:00 (Asia/Nicosia)
Online Session 16
Emerging Communications Systems
Room: Meeting Link
Chair: Mohammed Abegaz, Hamad Bin Khalifa University, Qatar, (mabegaz@hbku.edu.qa)
- 14:00 A Res-GRU Based Decoder for Polar Codes
- 14:12 Passive network monitoring and troubleshooting from within the browser: a data-driven approach
- 14:24 Cross-Layer Alarm Association Rules Discovery of Cloud-Network based on Knowledge Graph
- 14:36 Mixture of Experts for Intelligent Networks: A Large Language Model-enabled Approach
- 14:48 A Scalable Semantic Communication System Based on Meta-Learning
- 15:00 A Bayesian Optimization Algorithm to Improve the Spatial Reuse in the Next-Generation WLANs
- 15:12 Exploring the Frontiers of Firmware Fuzzing: μAFL's Application on Cortex M4 and Unix Programs
- 15:24 Deep Learning Image Classification Models for Solar Panels Dust Detection
- 15:36 Performance Analysis of Multi-Source Two-Way NOMA-AF Relaying Networks
- 15:48 What-if Analysis Framework for Digital Twins in 6G Wireless Network Management
Thursday, May 30
Thursday, May 30 9:00 - 11:00 (Asia/Nicosia)
On-site Session 9
UAVs
Room: Victory 1&2
Chair: Saad EL JAOUHARI, ISEP, France, (saad.el-jaouhari@isep.fr)
- 9:00 Signal quality detection in mobile network based on synthetic vehicle location data generation using generative adversial neural networks
- 9:20 Enhancing Secure Communication in 6G-Enabled IoV through UAV and Control Center Integration
- 9:40 Enhancing UAV Network Efficiency through 6G+Enabled Federated Learning Algorithms and Energy Optimization Techniques
- 10:00 Reinforcement Learning-based anti-Jamming Solution for Aerial-IRS-Aided Dense Dynamic Multi-User Environments
- 10:20 Deep Neural Quality of Service Prediction for Unmanned Aircraft System Communications
- 10:40 A Comparative Study on the Security of Kubernetes Deployments
Thursday, May 30 9:00 - 11:00 (Asia/Nicosia)
On-site Session 10
SDN
Room: Victory 3
Chair: Ibrahim Shaer, University of Western Ontario, Canada, (ishaer@uwo.ca)
- 9:00 LRS2: Improved Link Recovery in Software-Defined Networks with Stacked Generalization Ensemble
- 9:24 A Massive MIMO Sampling Detection Strategy Based on Denoising Diffusion Model
- 9:48 SDN-Enabled Cluster-based Evolving Graph Routing Scheme (SE-CEGRS)
- 10:12 Real-time Emergency Message Dissemination in IoV: A Cluster-based Approach with SDN and Fog Computing
- 10:36 Holochain-Based Secure and Energy Efficient IoT Network
Thursday, May 30 9:00 - 11:00 (Asia/Nicosia)
Online Session 17
Radio Communications
Room: Meeting Link (Copy this invitation and open in Tencent Meeting app (V2.13 or later) to join the meeting)
Chair: Yan Wei, Zhejiang University, China, (redwine447@zju.edu.cn)
- 9:00 A New Radio Frequency Fingerprint Identification Method Based on CEEMDAN
- 9:12 Advanced Techniques in Adaptive Beamforming for Enhanced DOA Estimation
- 9:24 Interference Analysis between 1800MHz NR System and Meteorological Satellites System Using ITU-R Model
- 9:36 Dynamic Interference Source Tracking Based on Motion State Decomposition
- 9:48 Combining AF-based Relay and Multiantenna for Over-the-Air Computation
- 10:00 A Novel Block Diagonalization Based Beam Nulling Method in Dynamic TDD Systems
- 10:12 Sparse Channel Estimation utilizing Optimal Wiener-Hopf Filtering in MIMO-OTFS Paradigm
- 10:24 Automatic Recognition of FM Signals Based on FFT Spectrum Analysis
- 10:36 Research on Adaptive Self-Interference Cancellation and Sensing Methods in ISAC System
- 10:48 A Novel Approach to Model the Scattering Environment in Channel Modeling for Integrated Sensing and Communications
Thursday, May 30 9:00 - 11:00 (Asia/Nicosia)
Online Session 18
- 9:00 Class-Incremental Learning for Baseband Modulation Classification: A Comparison
- 9:13 5G MIMO Antenna Design for Aerial Base Stations
- 9:26 Efficient Joint Hybrid Precoding and Analog Combining Scheme for Massive MIMO Systems
- 9:39 Pilot Contamination in Massive MIMO Systems: Challenges and Future Prospects
- 9:53 Deep Learning based Modeling of Wireless Communication Channel with Fading
- 10:06 A ML-based Spectrum Sharing Technique for Time-Sensitive Applications in Industrial Scenarios
- 10:19 A Study of Angle of Arrival Estimation of a RF Signal with FPGA Acceleration
- 10:33 Radio Frequency Fingerprinting in WBANs Using Complex-Valued Convolutional Neural Networks
- 10:46 Edge-Based Human Activity Recognition: A Novel Approach Using Spectral Analysis and Deep Learning
Thursday, May 30 9:00 - 11:00 (Asia/Nicosia)
Online Session 19
Applications
Room: Meeting Link (Passcode: 337701)
Chair: Yu Wang, Harbin Institute of Technology, (ywangee@163.com)
- 9:00 A Survey of Deep Learning Technology in Visual SLAM
- 9:13 A Review of Multimodal Sentiment Analysis: Modal Fusion and Representation
- 9:26 Efficient 3D Object Recognition for Unadjusted Bin Picking Automation
- 9:39 Context-Aware Hard and Slow Fall Detection
- 9:53 Robust Robot Formation Control Based on Streaming Communication and Leader-Follower Approach
- 10:06 EASR: Enabling Neural-Enhanced Video Streaming on Mobile Devices with Edge Assistance
- 10:19 CoarseUCB: A Context-Aware Bitrate Adaptation Algorithm for VBR-encoded Video Streaming
- 10:33 An Action Recognition Algorithm Based on Two-Stream Deep Learning for Metaverse Applications
- 10:46 Pose Estimation of Physiotherapy Exercises using ML Techniques
Thursday, May 30 9:00 - 11:00 (Asia/Nicosia)
Online Session 20
Internet Application
Room: Meeting Link (Passcode: 0Ymwyc)
Chair: Mohammed Jouhari, EMSI, Morocco, (jouhari4med@gmail.com)
- 9:00 Few-Shot Object Detection Algorithm Based on Geometric Prior and Attention RPN
- 9:13 Intelligent CSMA/CA for Wi-Fi networks
- 9:26 A Dynamic Redeployment System for Mobile Ambulances in Qatar, Empowered by Deep Reinforcement Learning
- 9:39 The Influence of Temporal Dependency on Training Algorithms for Spiking Neural Networks
- 9:53 Gesture-based notification system for Paralytics
- 10:06 A Transformer-Based Approach for Better Hand Gesture Recognition
- 10:19 Enhancing Precision in Tactile Internet-Enabled Remote Robotic Surgery: Kalman Filter Approach
- 10:33 AfriDial: African Dialect Model based on Deep Learning for Sentiment Analysis
- 10:46 Enhancing Movie Recommendations: A Deep Neural Network Approach with MovieLens Case Study
Thursday, May 30 11:30 - 13:00 (Asia/Nicosia)
Keynote 3: Telecom GPT: Next Generation AI powered Network
Merouane Debbah, IEEE Fellow
Room: Victory 1&2| Meeting Link (Passcode: 450359)
Chair: Mohsen Guizani, MBZUAI, UAE, (mguizani@gmail.com)
Thursday, May 30 14:00 - 16:00 (Asia/Nicosia)
On-site Session 11
Federated Communications
Room: Victory 1&2
Chair: Muhammad Jamal Shehab, Italy - Politecnico di Torino, Italy, (MuhammadShehab@ieee.org)
- 14:00 Network Slice Placement in Wireless Mesh Networks
- 14:20 FedLbs: Federated Learning Loss-Based Swapping Approach for Energy Building's Load Forecasting
- 14:40 Byzantine-Robust Federated Learning Based on Dynamic Gradient Filtering
- 15:00 SiamFLTP: Siamese Networks Empowered Federated Learning for Trajectory Prediction
- 15:20 Utility-Based Multipath Delivery of Prioritized XR Content in a Machine Learning and Network Slicing-enhanced Environment
Thursday, May 30 14:00 - 16:00 (Asia/Nicosia)
On-site Session 12
IoT Applications
Room: Victory 3
Chair: Ibrahim Shaer, UWO, Canada, (ishaer@uwo.ca)
- 14:00 Analyzing the Integration of 3D Building Digital Twins in Optimal IoT Networks Deployment
- 14:20 Model-based approach for efficient data exploitation process in IoT systems
- 14:40 Cross-layer Adaptable Contention Window for High-definition Map QoS Enhancement
- 15:00 A Hybrid HSV and YCrCb OpenCV-based Skin Tone Recognition Mechanism for Makeup Recommender Systems
- 15:20 Leveraging AI for Enhanced SemanticInteroperability in IoT: Insights from NER Models
- 15:40 Real time Twitter data sentiment analysis to predict the recession in the UK using Graph Neural Networks
Thursday, May 30 14:00 - 16:00 (Asia/Nicosia)
Online Session 21
Next-Generation Applications
Room: Meeting Link (Passcode: 51118)
Chair: Leyi Zhang, ZTE, China, (leyi.zhang@zte.com.cn)
- 14:00 Comprehensive Review of End-to-End Video Compression
- 14:13 Implementation of a Symmetric Double Arbiter-PUF and Evaluation the Impact of Temperature Influences using PYNQ-Z1 Board
- 14:26 NeRF-based Multi-View Synthesis Techniques: A Survey
- 14:39 A Deployment Method to Improve the Generalizability of Recurrent Neural Network
- 14:53 Adaptive cloud-based mobile video streaming service using real-time QoE estimation
- 15:06 Beyond Holographic Hybrid Precoding: New Role of Downlink Multiuser Interference
- 15:19 Establishing the Future of Work and Collaboration Through Institutional Metaverse
- 15:33 TinyML enabled smart parking dynamic slots computing and license plate recognition
- 15:46 Ontology Alignment: First Step towards Voice Control for Smart-Home Assistive Scenarios
Thursday, May 30 14:00 - 16:00 (Asia/Nicosia)
Online Session 22
IoT Applications I
Room: Meeting Link (Passcode: 2X7dSh)
Chair: Nahom Abishu Hayla, HBKU, Qatar, (nhayla@hbku.edu.qa)
- 14:00 An enhanced quality of service mechanism based on the two-way negotiation procedure
- 14:15 Evaluating Interference Impact on On-board Small Station Systems in Railway Networks
- 14:30 Advancing Railway Systems with Next-Generation 5G Connectivity
- 14:45 On Demand Reliability in the Internet of Things Enabled Sensors Networks
- 15:00 Link Quality Analysis for Buried Pipeline Monitoring using LoRa
- 15:15 The Optimization of Networked TT&C System for Mega LEO Constellation
- 15:30 Comparative Analysis of Fault-Localization Techniques in Adder
- 15:45 Enhancing Reliability in Smart Agriculture: Detecting Failures and Anomalies in Irrigation System
Thursday, May 30 14:00 - 16:00 (Asia/Nicosia)
Online Session 23
Mobile Communications
Room: Meeting Link
Chair: Zain ul Abideen Tariq, HBKU, Qatar, (zata28228@hbku.edu.qa)
- 14:00 A Kubernetes-Powered Personalized Federated Learning Platform for Resource-Constrained Internet of Medical Things
- 14:13 AI and IoT Uses, Challenges and Opportunities for e-Health: a review
- 14:26 Investigations on Wireless communication Transmission for Wireless Health Monitoring
- 14:39 Breast Cancer Segmentation in Mammograms using Antlion Optimization and CNN/GRU Architectures
- 14:53 Locating the Root Cause of Poor Coverage in Mobile Communication Networks Based on Spatio-temporal Graph Message Propagation
- 15:06 Improving NDN Resilience: A Novel Mitigation Mechanism Against Cache Pollution Attack
- 15:19 SemFusion: Multi-Source Semantic Information Fusion and Communication
- 15:33 Temporal-correlation Modeling for Improved CFO Estimation: The BiModule CFO Estimation (BMCE) Framework
- 15:46 Enhancing Privacy in Healthcare: A Multilevel Approach to (Pseudo)Anonymization
Thursday, May 30 14:00 - 16:00 (Asia/Nicosia)
Online Session 24
IoT Applications II
Room: Meeting Link (Passcode: 662940)
Chair: Elif Ak, Istanbul Technical University, Turkey, (akeli@itu.edu.tr)
- 14:00 An Improved Grey Wolf Optimizer for Task Scheduling in D2D-Assisted MEC Systems
- 14:15 Flat, Gateway-free, Infinite MANET Architecture with Variable Cell Size Cellular Barrage Relay Networks, and Geographic-Based Hazy Link State Routing
- 14:30 Analysis and Optimization: interference study of 900MHz NR system to NB-IoT system
- 14:45 A Task Bundling based Multi-Platform Cooperation Mechanism for Mobile Crowdsensing
- 15:00 Introducing the Concept of a Hybrid Navigation System Adapted to Blind Users for Optimal Stress-free Indoor and Outdoor Mobility
- 15:15 Enhancing IoT Intelligence: A Transformer-based Reinforcement Learning Methodology
- 15:30 Optimizing Efficiency Using a Low-Cost RFID-Based Inventory Management System
- 15:45 An Adaptive Data Rate scheme for multi-hop forwarding in LoRaWAN networks
- 16:00 Multi-Agent DRL-Based Multi-Objective Demand Response Optimization for Real-Time Energy Management in Smart Homes


